Bypass locked features on iOS apps with Burp Suite!
Written on December 13, 2019
In this post I will share some steps to enable blocked or hidden features on iOS app using Burp Suite tool.
I will use EWA, a language learning app on AppStore to illustrate the whole process.
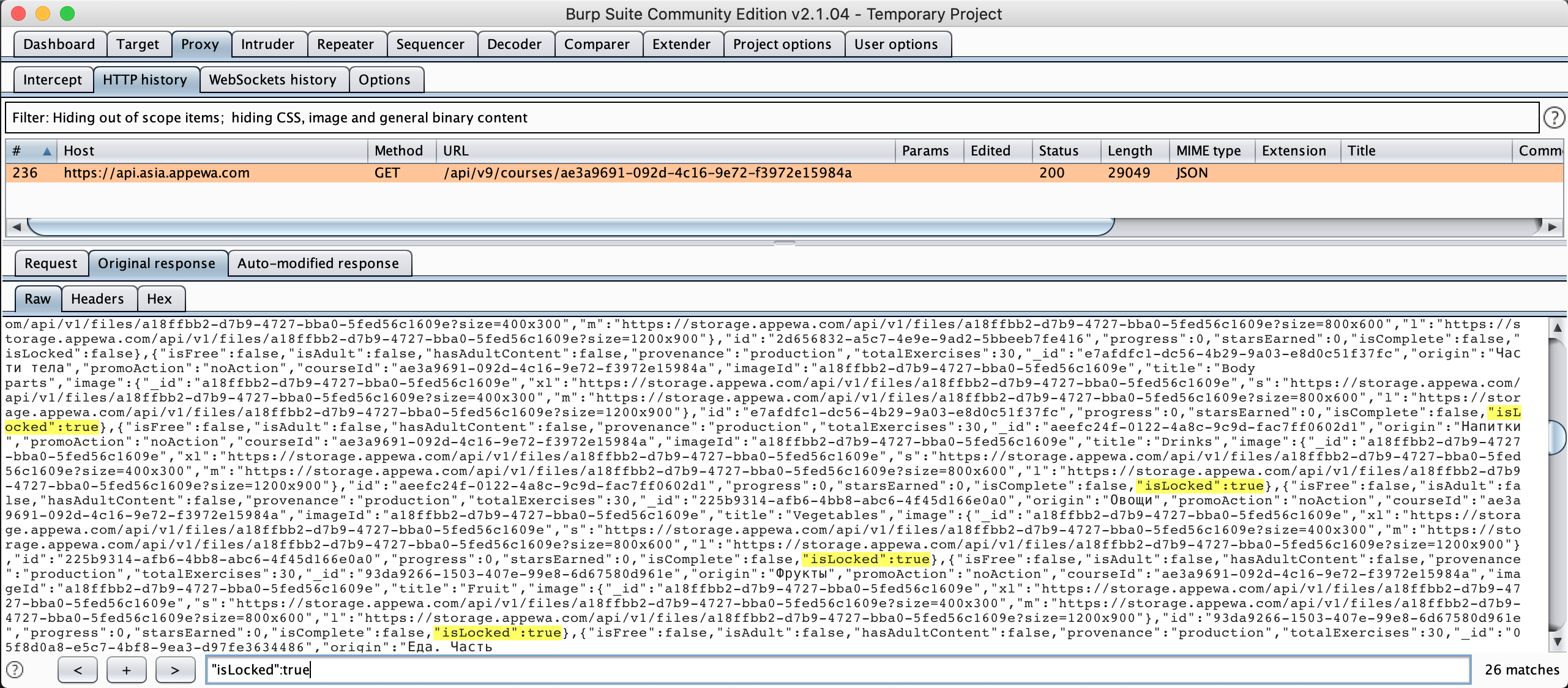
Figure 1: Burp Suite
Disclaimer
This post is for educational purposes only. How you use this information is your responsibility. I will not be held accountable for any illegal activities, so please use it at your discretion and contact the app’s author if you find issues.
Prerequisites
Below tools are used during this post:
- Download Burp Suite Community Edition
- Install EWA: Learn English & Spanish
- Installing Burp’s CA Certificate in an iOS Device
- Configuring an iOS Device to Work With Burp
Overview
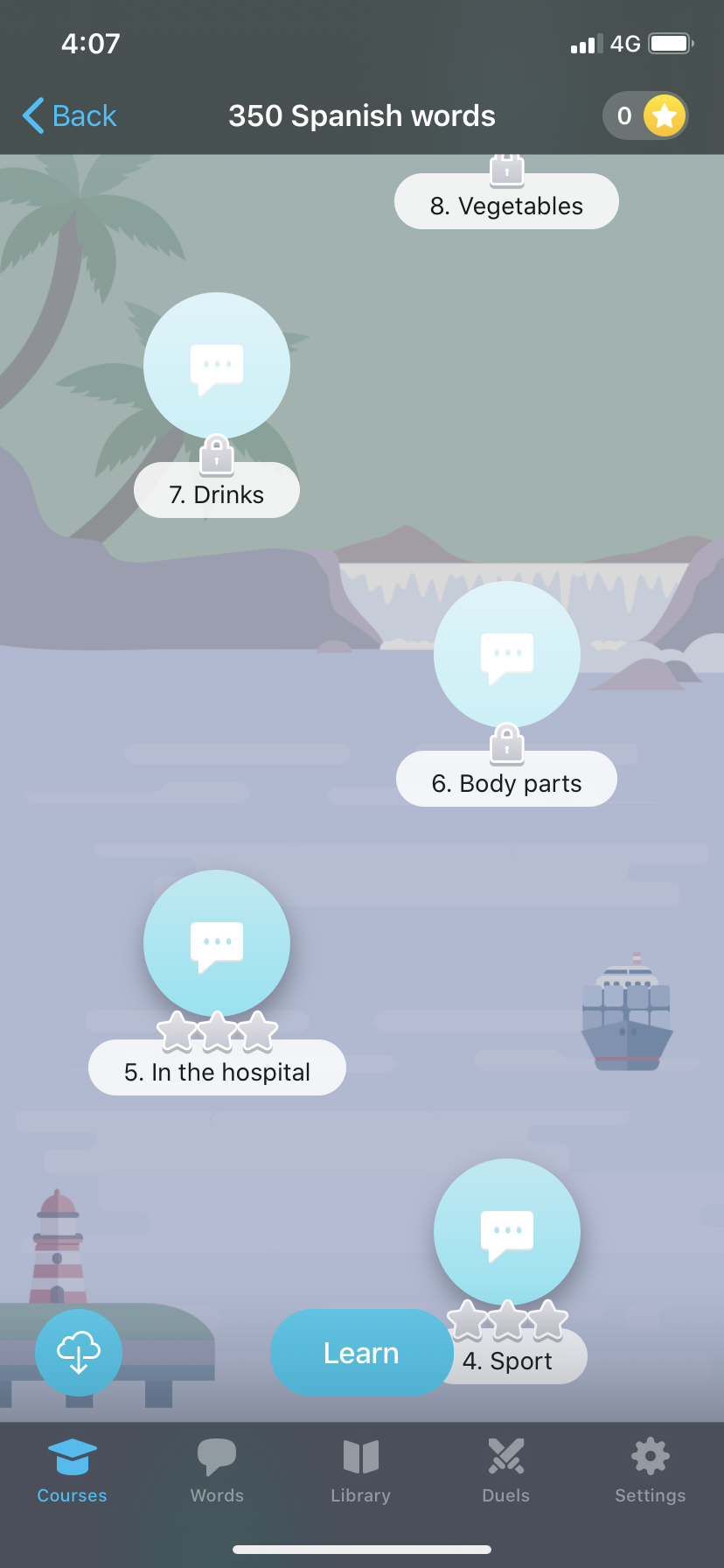
- Install and launch the app from App Store and landing to Courses screen then tap on 350 Spanish words card, we can see this app provides some free lessons (with star icon) and premium lessons (with lock icon).
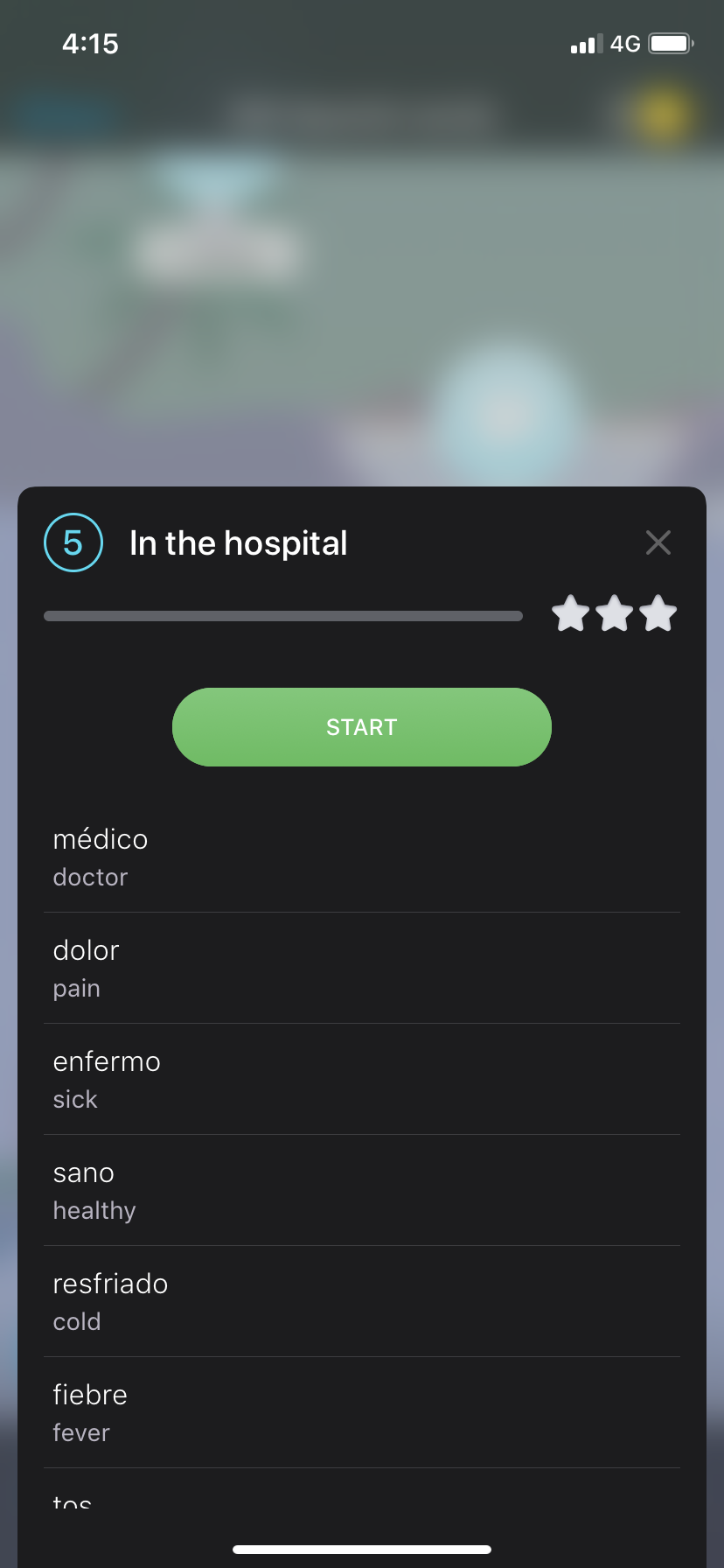
- When we tap on free lesson, let say 5. In the hospital one, we will see below screen prompted with words ready to learn :)
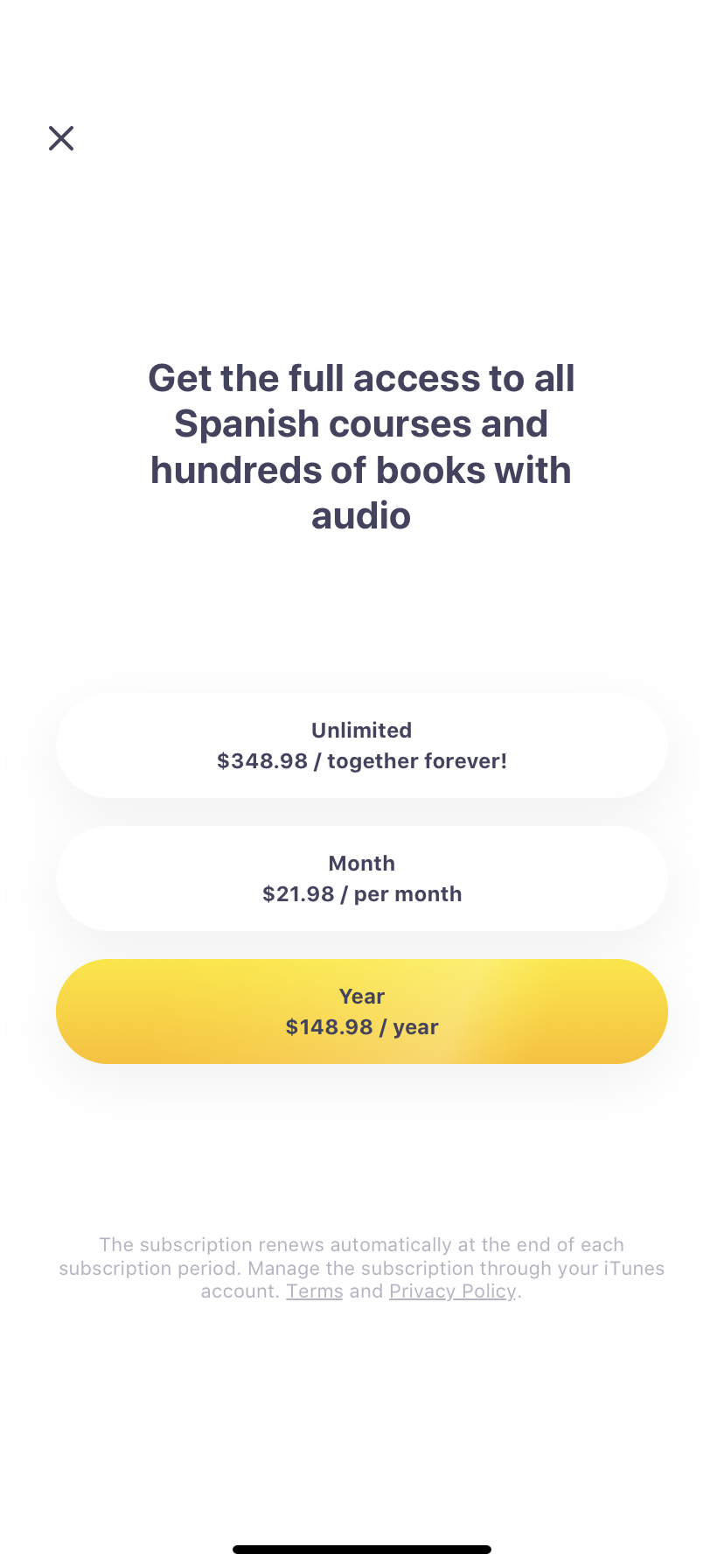
- But when we tap on locked lesson, let say 6. Body parts one, purchase screen will be shown instead and will ask us to subscribe before proceeding premium content :(
- We need to find the way to by pass client validation whether lesson is free or locked. Let’s do it!!!
Analysis
- Assume we already setup and configure iOS device to using laptop proxy as step in Prerequisites section.
- Install and launch the app from App Store and landing to Courses screen then tap on 350 Spanish words card, we can see this app provide some free lessons (with star icon) and premium lessons (with lock icon).
- Check Burp Proxy - HTTP History tab, you might notice there is request to server to fetch lessons details for tapped course (350 Spanish words) https://api.asia.appewa.com/api/v9/courses/ae3a9691-092d-4c16-9e72-f3972e15984a

Figure 5: Burp all lessons response body
- Look at Response tab, we can see response is in JSON format, take notes these 2 boolean attributes isFree & isLocked. These might be ones that tell client to show lock icon and purchase screen. Try to search “isLocked”:true or “isFree”:false we can see there are 26 matches which is matching with 26 lessons blocking on UI.
- To confirm if these 2 attributes used in client validation logic or not, we can use Burp to modify the these attributes value through proxy before reaching EWA iOS app. Thanks to Burp Match & Replace rules function, it provides the ability to find (or match) and replace certain parts of requests and responses.
- Follow this great article how to use replace & match rules, in this case we need to replace our Response body for “isLocked”:true -> “isLocked”:false and “isFree”:false -> “isFree”:true
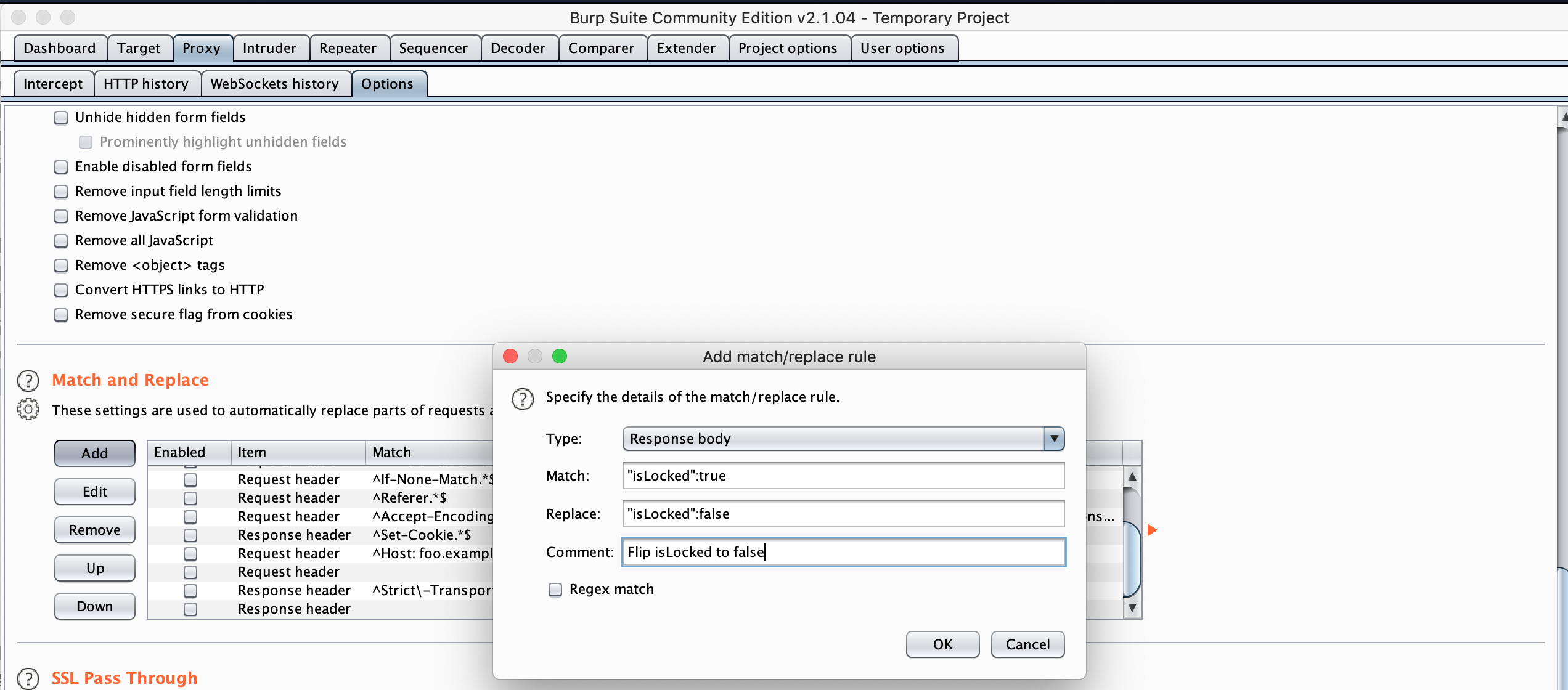
Figure 6: Add new match & replace rule
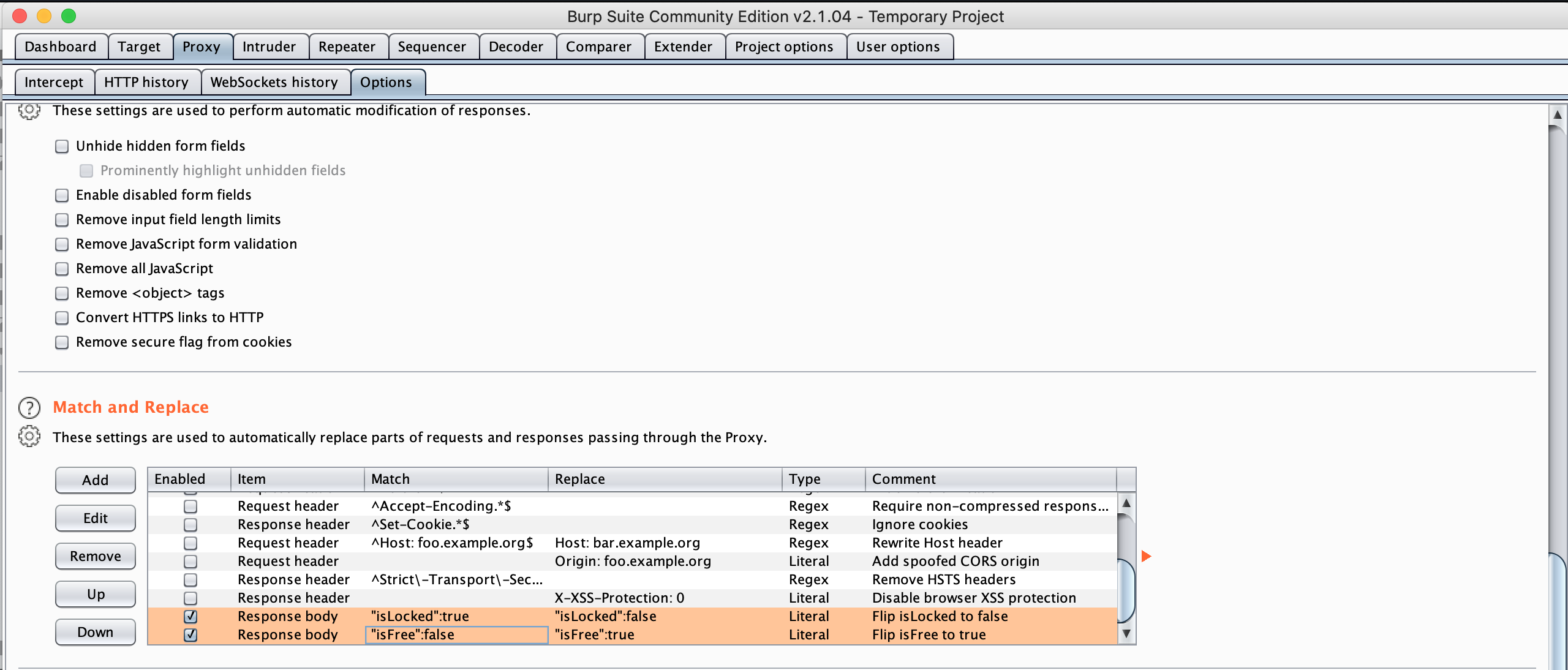
Figure 7: Apply new match & replace rules
- All setup is done, let try to send request again if response body is replaced or not. Please note EWA is caching request on server so if we try to make same request again, it wont return body data but response 304 not modified instead. So let reinstall the app and verify that request again. As you can see below, there will be new tab Auto-modified response, which mean response body is modified. Let further check by by searching “isLocked”:true we can see 0 matching results, double check on UI all lessons are UNLOCKED!!!!!!!
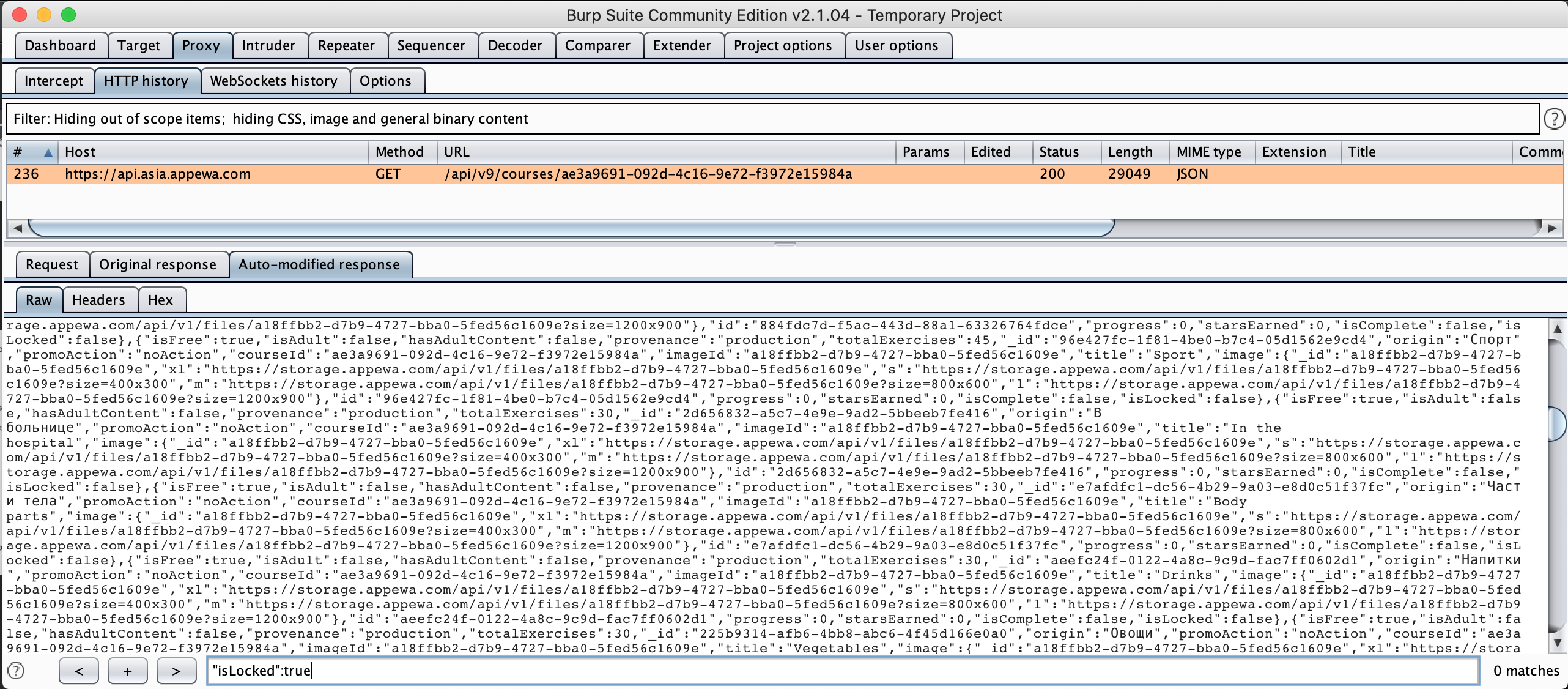
Figure 8: Auto modified response
- Let take step further by tapping on one locked lesson, we can see that it’s not loading words like free lesson. Checking response in Burp it’s showing “Access forbidden” message with error code 403, which make sense now as this premium content is not only protected at client but also at server.
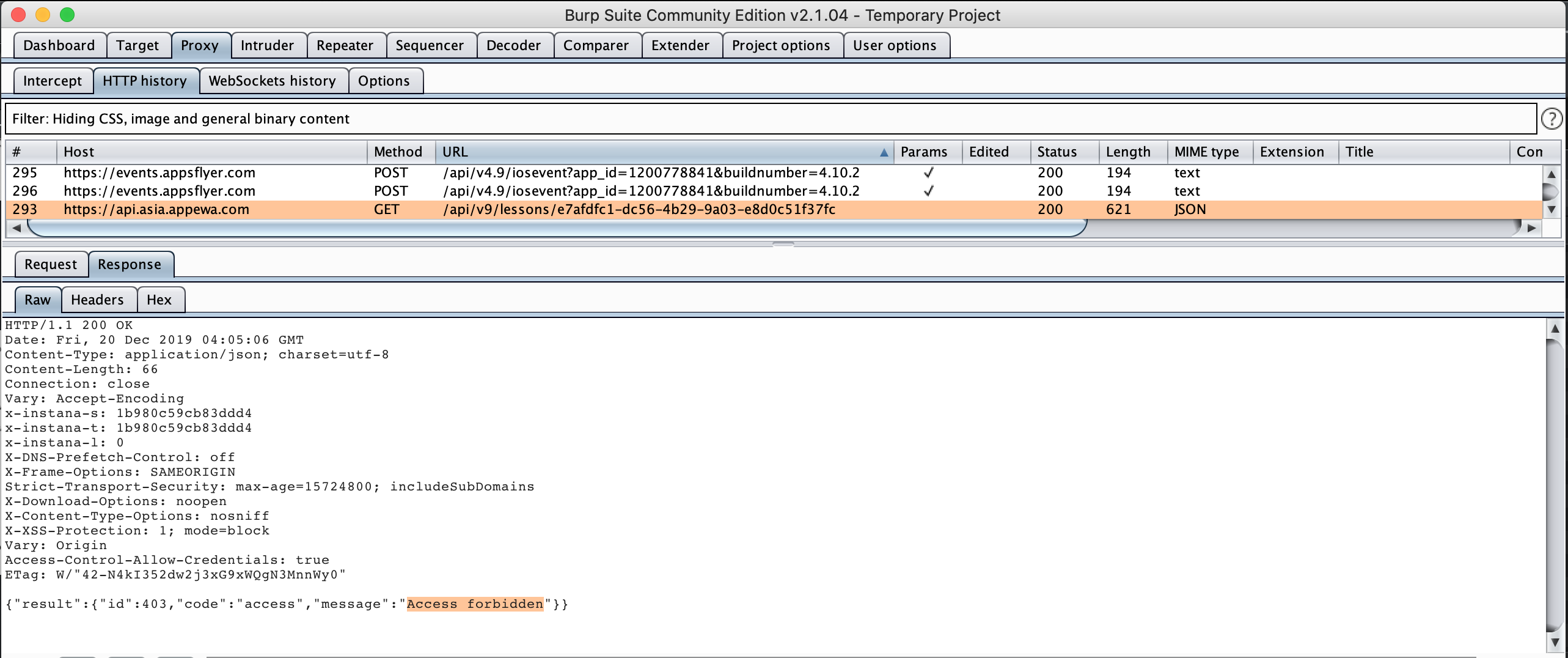
Figure 9: Access permission for premium content
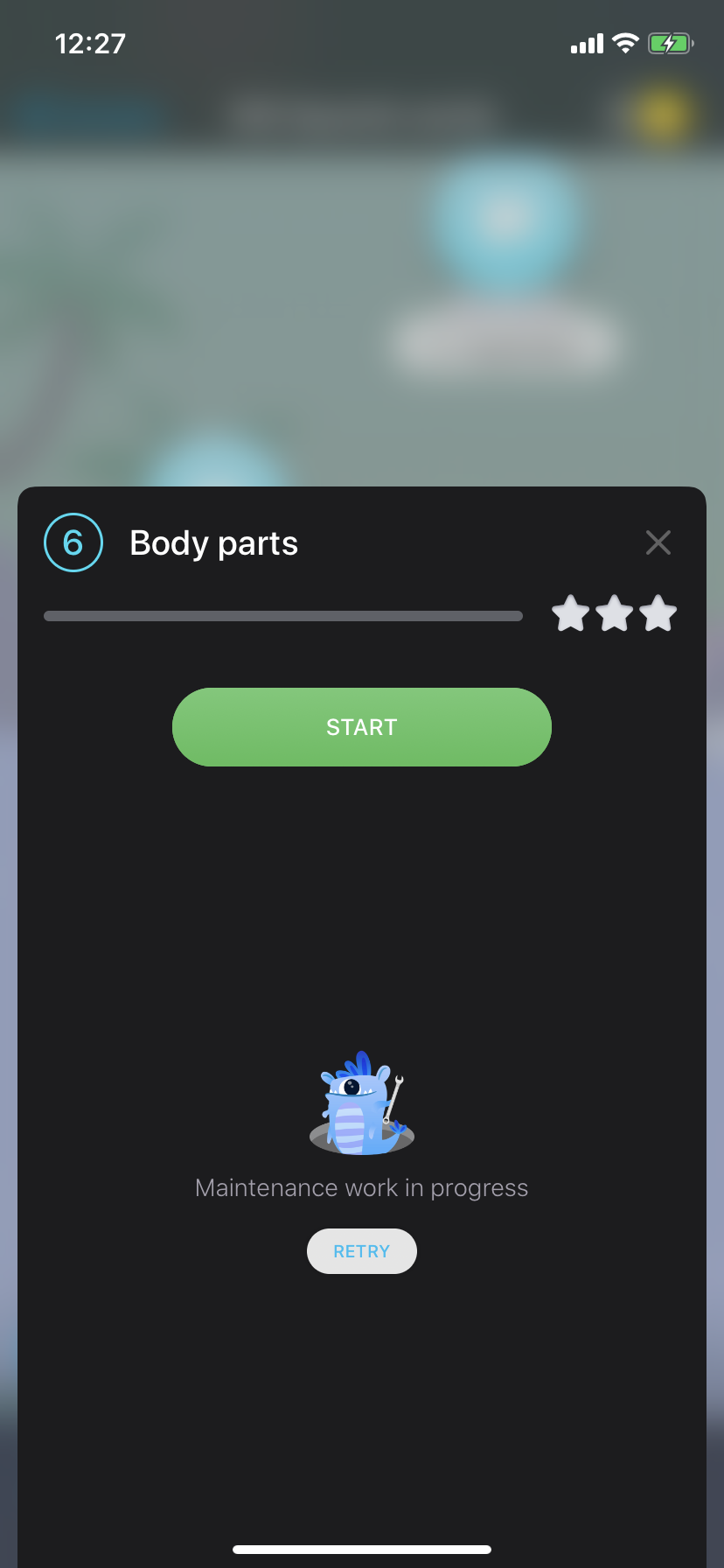
Figure 10: Premium lesson popup without any words
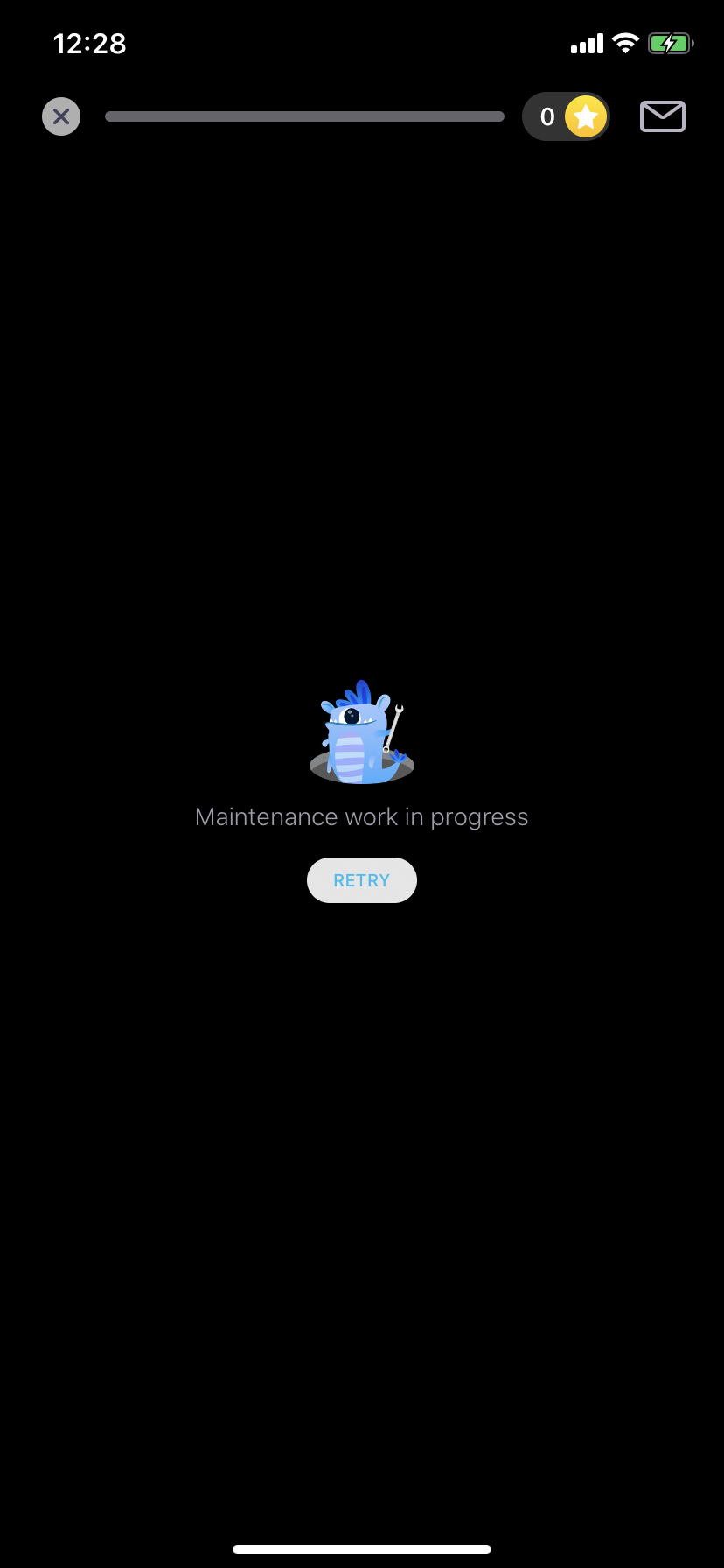
Figure 11: Premium lesson details without content
Summary
- Match & Replace rule is very useful to quickly identify which fields are used in app validation, then you might do further steps like write tweak for jailbreak or binary patching for permanent patch on non-jailbreak device.
- From developer side, client side validation is good but not enough. For apps with premium content it should be validated on server side also to mitigate app tampering.
- SSL Pinning can be employed on iOS app to prevent sniff and modify request/response payload, there are many tools and techniques to by pass SSL Pinning though.